Welcome to the world of hacking. Past decade has completely changed the way we live and perform our day to day work. Life in internet age is easy, simpler but vulnerable.
In the beginning it was fun for people to find loop holes in computers and show-off there skills. It was fun to write viruses and pop a friendly “happy birthday to me” message on your computer. Then came the age of writing viruses to harm people delete data on your machine infect your boot sector and propagate through floppy. It was followed by age of internet, whole new range of hacking tricks evolved.
In the beginning it was fun for people to find loop holes in computers and show-off there skills. It was fun to write viruses and pop a friendly “happy birthday to me” message on your computer. Then came the age of writing viruses to harm people delete data on your machine infect your boot sector and propagate through floppy. It was followed by age of internet, whole new range of hacking tricks evolved.
The thrill was not to show off your technical skills but to compromise individual systems and servers and gain information. Be it stealing credit card numbers from website or capturing user passwords through key-loggers. The motive had changed, it was no more technical show off, it was all about money. We now live in a time where money is not that important for hackers the targets has now shifted from individuals and websites to corporate and countries. In past one year we have noticed sophisticated attacks on corporate like Google and our own prime minister office (PMO). Anti-viruses and firewalls have been rendered ineffective, one click on a known URL can compromise your system, this is an era of cyber warfare rather we should call it an era of helplessness. The curious question is how hackers do it? How can I be one? Well …we try to explain few baby steps here…
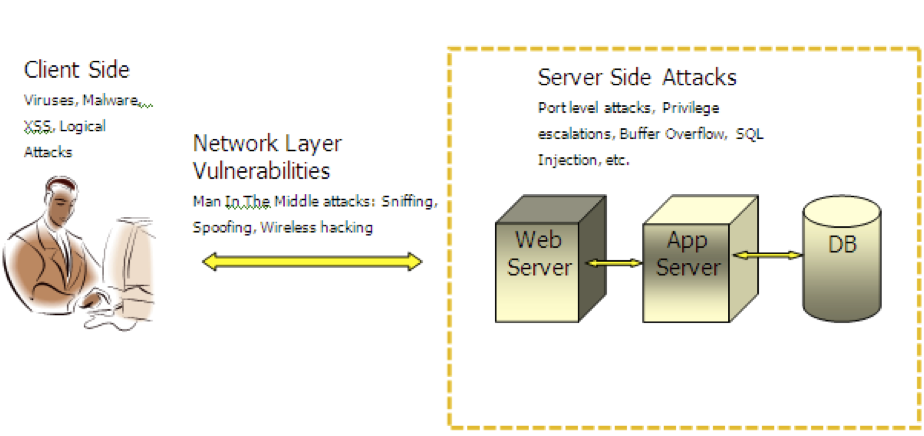
Below image shows typical web application architecture and corresponding vulnerabilities at each level.
Hacking at network or system level is a bit different from hacking at web application layer. But essentially hacking is 80% information gathering and 20% actual attack.
We give a brief of different phases of network/system layer hacking and corresponding tools used.
We give a brief of different phases of network/system layer hacking and corresponding tools used.
- . Foot printing
- Information Gathering (Whois, Nslookup, http://www.technicalinfo.net/tools, Google Hacking)
- Locate the network range (mostly in case of internal network) (Angry IP Scanner, Superscan)
. Scanning & Service Enumeration
- OS fingerprinting (xprobe) Detect ‘live’ systems on the network
- Detect Services running on target systems (Nmap)
- Detecting Vulnerable services (Nessus, Languard)
. Attack/Hacking
- Port Level Attacks (Meta Spoilt)
- Identifying vulnerability from Nessus report and finding corresponding exploits from sites like www.milw0rm.com, www.exploit-db.com etc.
. Spoofing and Sniffing
- Caine & Able
Similarly different phases and tools for web application layer hacking are:
1. Information Gathering
- Technology used (Java, .Net, PHP), message formats (JSON, XML, name/value pair)
- Finding what Webserver, APPServer, Application firewall are used?
2. Automated scanning
- Commercial tools:- Appscan, Acunetix, WebInspect, Cenzic, NTOSpider, Nstalker
- Open source: - W3AF, Paros, Webscarab, Burp, FireFox extensions like temper data, live http headers, XSSMe, SQLMe
3. Testing for OWASP top10 vulnerabilities
(http://www.owasp.org/index.php/Category:OWASP_Top_Ten_Project)
- Testing for XSS, SQL injection etc. using cheat sheets
- Attacks on business logic
4. Test for Configuration attacks
- Web server configuration attacks, like trying to open admin page for tomcat
- CMS admin pages trying to guess user id password for default admin page (Admin/Admin)
There are some well known Linux security distributions, which comes with most of the free tools installed. You can find more details from website www.securitydistro.com. Some of the highly recommended distros are:
- Backtrack (www.backtrack-linux.org)
- Matriux (http://www.matriux.com/)
- Moth (http://www.bonsai-sec.com/en/research/moth.php)
- Unlatched Windows 2000, Xp (sp2)
- Damn Vulnerable Linux
- de-ice distributions
- Hackerdemia
- pWnOS
- WebGoat (www.owasp.org)
- Hacme Tools (bank, Casion, Books, Travel)
- Damm vulnerable app
- Jarlsberg
- http://demo.testfire.net/
- http://testasp.acunetix.com/
References
- www.owasp.org/index.php/Phoenix/Tools
- www.webappsec.org
- www.seclists.org/
Disclaimer
The information provided in this article is purely for educational purpose and for computer security awareness. The views expressed in this article are purely based on my experience and does not reflect the views of my present or past employers. The author does not promote computer hacking in any way or the misuse of this information against any individual or organization. Computer hacking and identity theft is a punishable offense. The author can not be held liable for any kind of damages done whatsoever to your machine, or damages caused by the use of information provided in this article. By reading this article you agree to those terms.
 RSS Feed
RSS Feed